As industries continue to adapt to new technologies, regulations, and market de....
Evolving Cyberattacks - The Escape

Why are sophisticated techniques failing to defend companies from Cyberattacks?
As the introduction of the internet has created a new battlefield, you can have world-class firewalls, or keep your system updated with the latest anti-virus software releases, and yet your business will not be immune to data breaches, cyberattacks, and internal threats.
A study conducted by the Ponemon Institute in 2016, exemplifies the fact that cyber attackers are winning over “defenders” as they are exploiting the vulnerabilities much faster than defenders are mitigating them. The study revealed that 55 percent of small businesses have been subject to a cyberattack in the previous year, while 50 percent said they were victims to a data breach during this year.
However, cyberattacks do not account for the largest part of the SMB data breaches. The Ponemon survey confirmed that 41 percent of SMBs data were compromised due to mistakes made by negligent employees, contactors, and also third-parties.
Moreover, according to EUROPOL, IOCTA 2017 Assessment, a portion of the announced cyber-attacks from mid-2017 represents this pattern. For authentic financially motivated attacks, exertion remains a typical strategy, with ransomware and Distributed Denial of Service (DDoS) attacks remaining needs for EU law enforcement. Europol claimed that CNI firms should be "better instructed, prepared and equipped to manage these attacks", using the GDPR and NIS Directive to enhance baseline security. It added that law enforcement’s “prevention and awareness” strategies needed to adapt to the growth of social engineering as an "essential tactic".
Ilia Kolochenko, the CEO of High-Tech Bridge, argued that ransomware will be around for at least another decade. He added that “Many organizations and individuals have abandoned machines they have not updated for years for various reasons, from overt negligence to complicated business processes and compliance. Worse, many large companies and governmental organizations don’t even have a comprehensive and up-to-date inventory of their digital assets, and are not even aware that such systems exist.”
Why should organizations consider a cybersecurity awareness training program?
Given that attackers have attained a level of sophistication that cannot be resolved by using traditional defensive strategies, it is important to focus on educating users, as they are the key components in cyber security. If users lack proper awareness and education on how to utilize cyber means in their daily operations, your defense system will have a massive gap and security controls will fail to be effective. This modern era of cyberattacks expects clients to participate in the cyber protection of the organization, and the greatest mistake that organizations seem to make is to rely only on sophisticated technology and software as cyber-defense mechanisms.
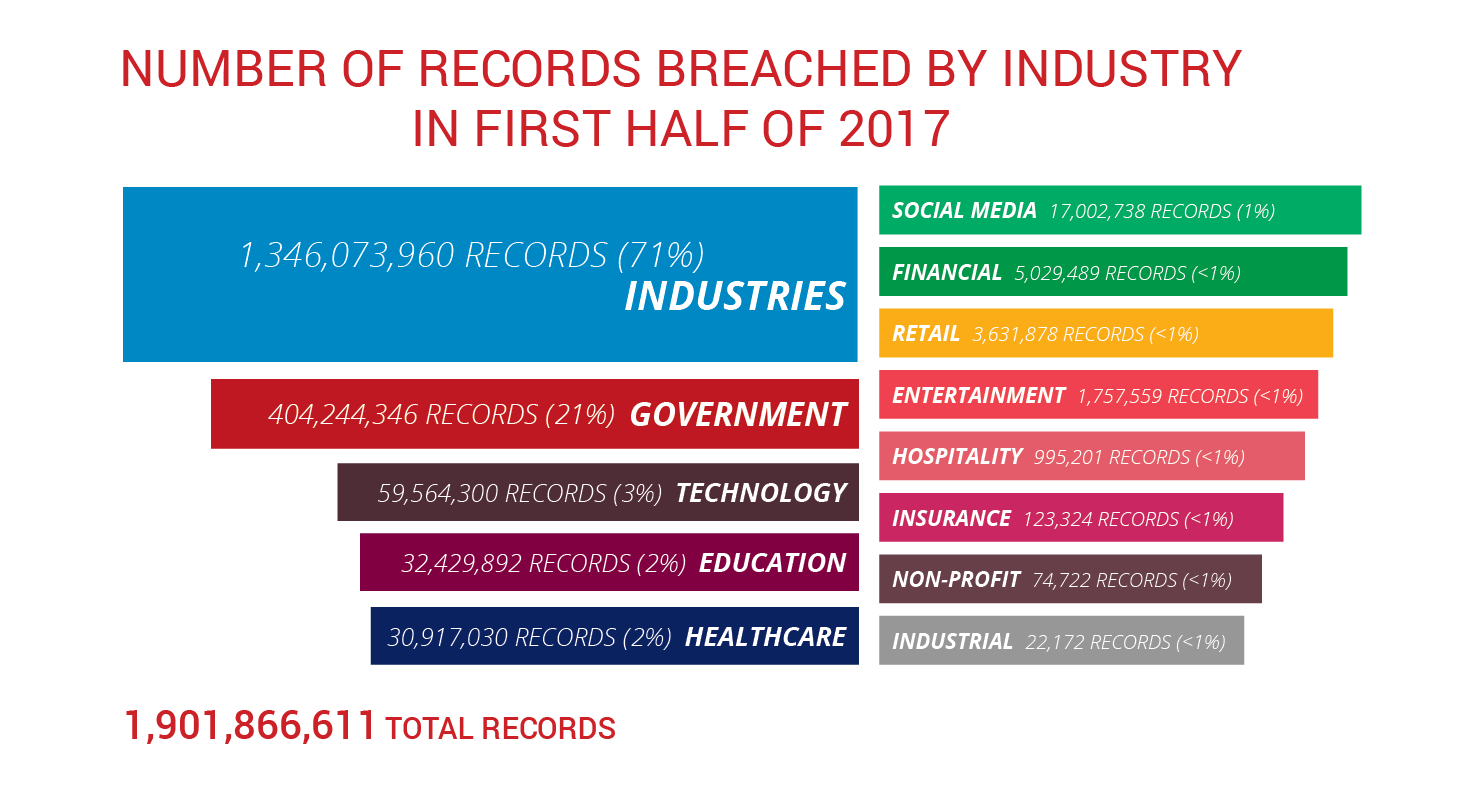
Figure 1. Statistics regarding data breaches - January 2017 until June 2017
Phishing attacks account for 91 percent of data breaches, and if users are not prepared to recognize and properly respond to these attacks, the danger of an effective breach or malware attack, for example ransomware, is significantly increased.
That being said, organizations should implement a policy on employee cyber-security awareness, and acknowledge the cyber-security awareness as an active cyber defense measure that facilitates the fight against cyber threats. Considering the unavoidable financial, productivity and reputation costs incurred due to an information theft, a prior well thought plan on how to manage these situations should be established.
In this case, the ISO/IEC 27032 standard gives guidelines and explanations on how companies can ensure safer data processing. There are security issues that are not covered by current information security, network security and security application, as there are gaps between these domains as a result of poor communication between the organizations. Therefore, this International Standard addresses Cyberspace security or Cybersecurity issues by bridging the gaps between different security domains in Cyberspace. Get certified by PECB through Cybersecurity Management Training Courses.
Author: Ardian Berisha is the Portfolio Marketing Manager for Information Security Management at PECB. He is in charge of conducting market research while developing and providing information related to ISM standards. If you have any questions, please do not hesitate to contact him: marketing.ism@pecb.com.
Co-Author: Albion Bikliqi is the PECB’s Information Security Manager. He is the key person or the process owner for all the activities pertaining to protecting the confidentiality and integrity of any related business data that is of great significance to the organization. While carrying out these ongoing activities, he ensures that the organization's rules and regulations are being adhered by the employees. If you have any questions, please do not hesitate to contact him: information.security@pecb.com.


